Abstract
Bitcoin faces a critical governance asymmetry: while its technical consensus layer is cryptographically bulletproof, its development governance relies on informal social coordination. At Bitcoin's multi-trillion dollar scale, this represents an existential vulnerability.
This whitepaper presents two innovations that enable each other: BLVM provides mathematical rigor (proofs locked to code, formal verification, consensus matching); Bitcoin Commons provides governance coordination without civil war (Ostrom's principles through cryptographic enforcement). Together they solve Bitcoin's governance asymmetry.
The system is being developed across six public repositories, with work ongoing on mathematical specifications, governance infrastructure, and economic sustainability. This is a living document: the foundation exists, but its future depends on community contribution. For the complete narrative treatment, see Bitcoin Commons: Decentralizing the Decentralizers.
1. Introduction
Bitcoin solved Byzantine consensus between strangers (Nakamoto, 2008) but ignored consensus between developers. The network's substantial market capitalization demands institutional maturity matching its technical excellence.
The original cypherpunk developers focused on eliminating trusted third parties in transactions but inadvertently created trusted parties in development. Bitcoin Commons addresses Bitcoin's most critical vulnerability: governance asymmetry between technical consensus and development coordination.
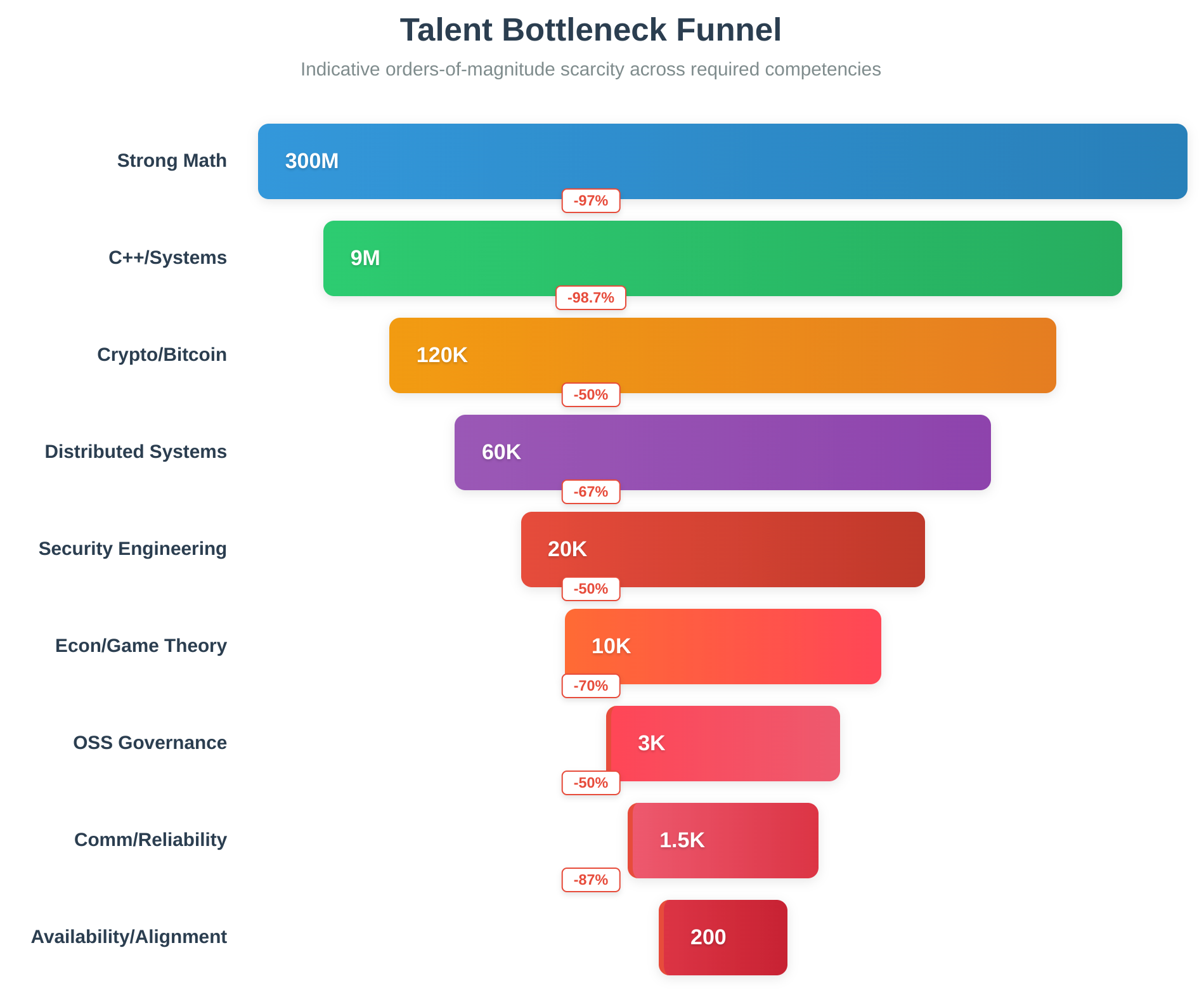
1.1 The Talent Bottleneck: Orders of Magnitude and Sources
Bitcoin development draws on multiple hard domains simultaneously (C++, applied cryptography, distributed systems, security engineering, economics/game theory, and open-source governance). Each extra domain narrows the pool. Using conservative, sourced baselines and clearly labeled assumptions, we estimate the rarity of a contributor who combines these competencies and is available to work on Bitcoin:
Assumptions and sources:
- World population baseline: ~8.1B (UN DESA, World Population Prospects, 2022 Rev.)
- Global developers: ~30M-47M (range spanning widely cited industry estimates, incl. SlashData and similar studies)
- C++ share of developers: ~15%-25% (range spanning major annual developer surveys)
- Adult numeracy (problem-solving proficiency): on the order of 10%-20% globally (OECD PIAAC cross-country evidence; global extrapolation is approximate)
- Bitcoin Core maintainers: single-digit individuals; contributors: hundreds (public repo statistics)
Rarity funnel (indicative, overlapping, not strictly independent):
- Strong college-level math (calculus/linear algebra): 3%-5% of population, resulting in 240M-400M
- Professional developers: ~30M-47M (subset, separate baseline)
- C++/systems competency: 15%-25% of developers → 4.5M-11.8M
- Applied cryptography + Bitcoin protocol literacy: 1%-2% of C++ devs → 45k-236k
- Distributed systems/P2P networking depth: 30%-50% → 13.5k-118k
- Security engineering mindset (memory safety, adversarial thinking): 20%-30% → 2.7k-35k
- Economics/game-theory literacy: 30%-50%, resulting in 0.8k-17.5k
- Open-source governance (review culture, consensus norms): 10%-30%, resulting in 80-5k
- Communication/reliability under public scrutiny: 30%-50% → 24-2.5k
- Availability/alignment to work on Bitcoin: 10%-30% → ~2-750
Interpretation:
- Even with generous ranges, the intersection yields on the order of dozens to a few hundred globally available individuals with the full stack to work reliably on Bitcoin's most sensitive layers.
- Public data corroborates scarcity at the tip: Bitcoin Core has hundreds of credited contributors but only a small, rotating single-digit maintainer set. This human bottleneck contrasts with the cryptographic abundance at the consensus layer.
Citations (illustrative anchors):
- UN DESA, World Population Prospects (2022)
- SlashData, Global Developer Population Trends
- Annual developer surveys (Stack Overflow) for C++ usage
- OECD PIAAC, adult skills numeracy distributions
- Bitcoin Core repository statistics (GitHub)
2. Problem Statement
Technical Reality
Bitcoin's consensus rules are embedded in 350,000+ lines of C++ code with no mathematical specification. Bitcoin Core maintains 99.5% market share among implementations, creating effective monopoly control over Bitcoin's evolution. The lack of formal specification makes it impossible to build safe alternative implementations or verify consensus correctness.
Governance Reality
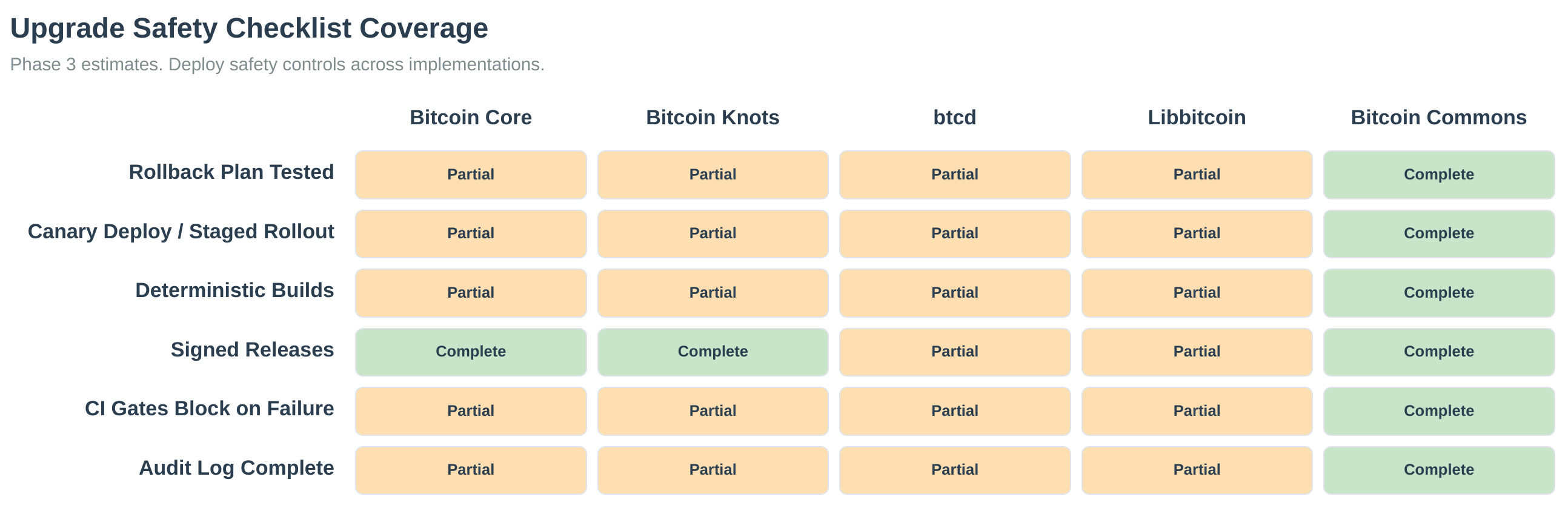
Bitcoin's development governance relies entirely on informal social coordination. No systematic consequences exist for bad actors, no formal dispute resolution mechanisms exist, and power is invisible and unaccountable. The system is vulnerable to capture through relationships rather than rules. Quantitative analysis of Bitcoin Core's development patterns reveals significant power concentration: the top 3 maintainers control 81.1% of merges, self-merge rates reach 26.5%, and review quality varies substantially with zero-review merges historically at 30.2% (bitcoin-governance-research, 2026). Network analysis reveals structural misalignments between technical development and social infrastructure, creating coordination gaps that prevent effective governance (Hough, 2025). These patterns reflect the paradox of embeddedness in network structures, where relationships can inhibit coordination and reinforce existing power dynamics (Uzzi, 1997). Funding may not flow to projects with strong grassroots activity, and "rich-get-richer" dynamics reinforce existing patterns rather than enabling competition. Commons addresses these issues through cryptographic enforcement of multisig thresholds, mandatory review periods, and transparent accountability mechanisms.
Historical Context
Early developers recognized this problem. Gavin Andresen (2014) raised governance concerns but was marginalized during blocksize wars. Mike Hearn attempted governance solutions but proposed hierarchical models inappropriate for Bitcoin's decentralized ethos. Academic researchers (De Filippi & Loveluck, 2016) documented these power structures but provided no actionable solutions.
Scale Considerations
Bitcoin's growth from early stages to multi-trillion dollar scale requires institutional reform. The next crisis, whether AI attacks, regulatory capture, or internal conflicts, won't wait for the community to develop governance solutions reactively.
3. Theoretical Framework: The Triple Foundation
Bitcoin Commons synthesizes three distinct theoretical frameworks, each addressing weaknesses in the others to create governance architecture stronger than any single approach alone.
Framework 1: Elinor Ostrom - Commons Governance
Elinor Ostrom won the 2009 Nobel Prize in Economics for proving that shared resources don't inevitably collapse into chaos or capture (Ostrom, 1990). Her research documented principles for governing commons without central authority across centuries of real-world examples.
Ostrom's (1990) Seven Principles.
- Clear boundaries on who decides what. Defined decision-making authority.
- Consequences for violations. Systematic enforcement mechanisms.
- Local dispute resolution. Formal conflict resolution processes.
- Protection from external interference. Resistance to outside pressure.
- Collective choice arrangements. Meaningful participation in rule-making.
- Graduated sanctions. Proportional consequences for violations.
- Monitoring and accountability. Transparent oversight mechanisms.
What This Provides. Proven institutional design for shared resources, evidence decentralized governance works, and coordination without hierarchy.
Framework 2: F.A. Hayek - Spontaneous Order
Friedrich Hayek's Austrian economics provides the competitive discovery mechanism that enables governance evolution rather than rigid design.
Hayek's Core Insights.
- Dispersed Knowledge Problem. No central planner can know what's needed because knowledge is distributed across many actors.
- Competition as Discovery. Competition reveals information that couldn't be known in advance.
- Spontaneous Order. Best institutions emerge through evolution, not top-down design.
- Markets Need Infrastructure. Competition requires actual alternatives to compete.
What This Provides. Justification for avoiding central planning, competitive governance discovery, and institutions that evolve through market signals.
Framework 3: Bitcoin - Cryptographic Enforcement
Bitcoin's innovation provides the enforcement tools that make decentralized governance work at scale without trusted parties.
Bitcoin's Core Principles.
- Don't Trust, Verify. Cryptographic enforcement replaces social trust.
- Permissionless Innovation. Anyone can build without asking permission.
- Exit Rights. Fork option provides ultimate check on power.
- Decentralized Control. No single point of authority.
What This Provides. Tools for enforcing rules without trust, proof decentralized systems work at scale, and a model for implementing Hayek's principles digitally.
The Triple Synthesis
The three frameworks address each other's weaknesses:
Ostrom's Challenge. Commons governance historically relied on social pressure, vulnerable to capture at scale.
Bitcoin's Solution. Cryptographic enforcement replaces social pressure with mathematical proof.
Hayek's Challenge. Competition discovers optimal solutions but requires actual alternatives to compete.
Ostrom's Solution. Provides institutional framework for multiple governance models to coexist.
Bitcoin's Challenge. Solved technical consensus but not social governance.
Hayek + Ostrom Solution. Competitive discovery of governance models using proven institutional principles.
The Result. Governance that is proven (Ostrom's research), evolving (Hayek's competition), and enforceable (Bitcoin's cryptography).
Cryptographic Polycentrism: The Governance Model
Bitcoin Commons implements Cryptographic Polycentrism, a governance model that creates multiple centers of power with clear boundaries, enforced through cryptography rather than social pressure. This approach applies Ostrom's proven principles using Bitcoin's cryptographic enforcement tools, enabling competitive discovery through Hayekian market mechanisms while maintaining Ostrom's institutional structure.
Cryptographic Polycentrism differs from traditional polycentrism (multiple decision centers) by using cryptographic enforcement to make boundaries mathematically verifiable rather than socially negotiated. Where traditional governance relies on trust and reputation, Cryptographic Polycentrism uses multisig thresholds, mandatory review periods, and three-layer verification providing real-time transparency and immutable proof to create enforceable boundaries that cannot be bypassed even by repository administrators.
This model enables multiple implementations to compete (Hayek's discovery mechanism) while maintaining clear institutional boundaries (Ostrom's principles) through cryptographic proof (Bitcoin's innovation). The result is governance that is both competitive and accountable, proven and evolving, decentralized and enforceable.
Bitcoin Core's Current State
Bitcoin Core has informal implementations of some Ostrom (1990) principles but lacks systematic enforcement.
Mapping The Principles to Implementation
The modular architecture implements Ostrom's seven principles through cryptographic enforcement rather than social pressure. The chart below shows how these principles integrate with principles from Hayek, Bitcoin, and Cypherpunk frameworks:
Principle 1. Clear Boundaries.
- Layers. Base (network consensus), Module (user choice).
- Implementation. Architecture enforces boundaries. Modules cannot modify consensus code paths.
Principle 2. Consequences for Violations.
- Technical/Reputational. Module quality standards, transparent adoption metrics, cryptographic enforcement.
- Implementation. Cryptographic enforcement makes consequences automatic, not social.
Principle 3. Local Dispute Resolution.
- Architecture-based. Competing modules resolve disputes. User choice determines winners. Module conflicts don't threaten consensus.
- Implementation. No central arbiter needed. Architecture provides resolution through user configuration.
Principle 4. Protection from External Interference.
- Self-Funding/Multi-jurisdictional/Fork-Ready. Operational revenue modules, distributed keyholders, governance fork capability.
- Implementation. Cryptographic multisig ensures no single jurisdiction can compel action.
Principle 5. Collective Choice Arrangements.
- User sovereignty via configuration. Users compose stacks. Adoption metrics function as voting. Participation through choices, not committees.
- Implementation. GUI-based module selection enables collective choice through user preferences.
Principle 6. Graduated Sanctions.
- Proportional escalation. Moderate fork to major deprecation to governance fork. Graduated signature requirements (2-of-3 to 6-of-7). Sanctions at module layer, no consensus changes required.
- Implementation. Multisig thresholds vary by change category (2-of-3 extension to 6-of-7 constitutional).
Principle 7. Monitoring and Accountability.
- Cryptographic transparency. All governance actions signed and verifiable. Module adoption, revenue flows, decision provenance auditable. Three-layer verification ensures complete audit trails.
- Implementation. Automated monitoring through cryptographic verification, not social trust.
Comparison with Bitcoin Core.
Bitcoin Core has informal implementations of some Ostrom principles but lacks systematic enforcement. Quantitative analysis reveals power concentration where top maintainers control 81.1% of merges, self-merge rates reach 26.5%, and review quality varies substantially. The system has informal boundaries (Core maintainers, BIP editors) but no formal process for selection, removal, or authority limits. Social pressure and reputation damage provide consequences, but there's no systematic enforcement mechanism. Most critically, there's no infrastructure for competitive discovery. Bitcoin Core's 99.5% market share prevents Hayekian competition from working. Below is a detailed comparison:
- Clear Boundaries. Informal (maintainers, BIP editors), no formal selection/removal process. Commons Solution. Cryptographic multisig thresholds define authority limits. Maintainer selection/removal requires constitutional-level approval (6-of-7 signatures).
- Consequences. Social pressure only, no systematic enforcement. Commons Solution. Cryptographic enforcement prevents merges without required signatures. Violations are mathematically impossible, not socially discouraged.
- Dispute Resolution. BIP process advisory only, no binding mechanism. Commons Solution. Three-layer verification provides cryptographic proof for dispute resolution. Governance actions are cryptographically verifiable and timestamped.
- External Protection. No systematic protection, individuals can be pressured. Commons Solution. Push-only architecture with VPN isolation. No incoming HTTP endpoints. Cryptographic requirements cannot be bypassed even by repository admins.
- Collective Choice. BIP process exists but no formal consensus mechanism. Commons Solution. Tiered multisig thresholds (2-of-3 to 6-of-7) with mandatory review periods. Governance actions require explicit cryptographic approval from multiple maintainers.
- Graduated Sanctions. Informal social pressure, no systematic escalation. Commons Solution. Tiered signature requirements escalate with risk level. Emergency situations require higher thresholds (4-of-5, 5-of-5) with automatic expiration.
- Monitoring. Public GitHub/mailing lists, no formal accountability system. Commons Solution. Three-layer verification provides real-time transparency, immutable proof, and merge control. All governance actions are cryptographically signed and verifiable.
The pattern: Bitcoin Core has informal implementations that worked at billion-scale but become vulnerable at multi-trillion scale. Commons implements all seven Ostrom principles through Cryptographic Polycentrism, directly addressing the power concentration and accountability gaps identified in quantitative analysis (bitcoin-governance-research, 2026).
4. Technical Solution: The Orange Paper
Problem
Bitcoin's consensus rules lack mathematical specification (embedded in 350,000+ lines of C++ code with no formal specification). This makes them impossible to verify, understand, or implement independently. The 2018 inflation bug (CVE-2018-17144) existed in Bitcoin Core for years before discovery. This is exactly the class of error formal verification eliminates.
Solution
The Orange Paper provides a formal mathematical specification of Bitcoin's consensus protocol through AI-assisted extraction from Bitcoin Core's codebase. The specification includes:
- Mathematical foundations (set theory, cryptographic primitives, network protocols)
- State transition functions (block validation, transaction validation, consensus rules)
- Economic model (mining rewards, fee calculations, difficulty adjustment)
- Security properties (Byzantine fault tolerance, Sybil resistance, double-spending prevention)
Benefits
- Safe alternative implementations: Independent implementations can verify against mathematical specification
- Formal verification: Consensus correctness can be mathematically proven
- Reduced consensus bugs: Systematic analysis eliminates entire classes of errors
- Technical moat: AI extraction eliminates "not invented here" bias
AI-Assisted Extraction Methodology
The Orange Paper uses AI-assisted extraction from Bitcoin Core's codebase to formalize consensus rules. This approach:
- Analyzes Bitcoin Core's codebase to identify consensus-critical code paths
- Extracts mathematical relationships from implementation details
- Creates formal specifications that are independent of specific code structure
- Enables verification that specification matches actual network behavior
Proof Maintenance and Specification Quality
The formal verification process includes ongoing maintenance to ensure specification accuracy:
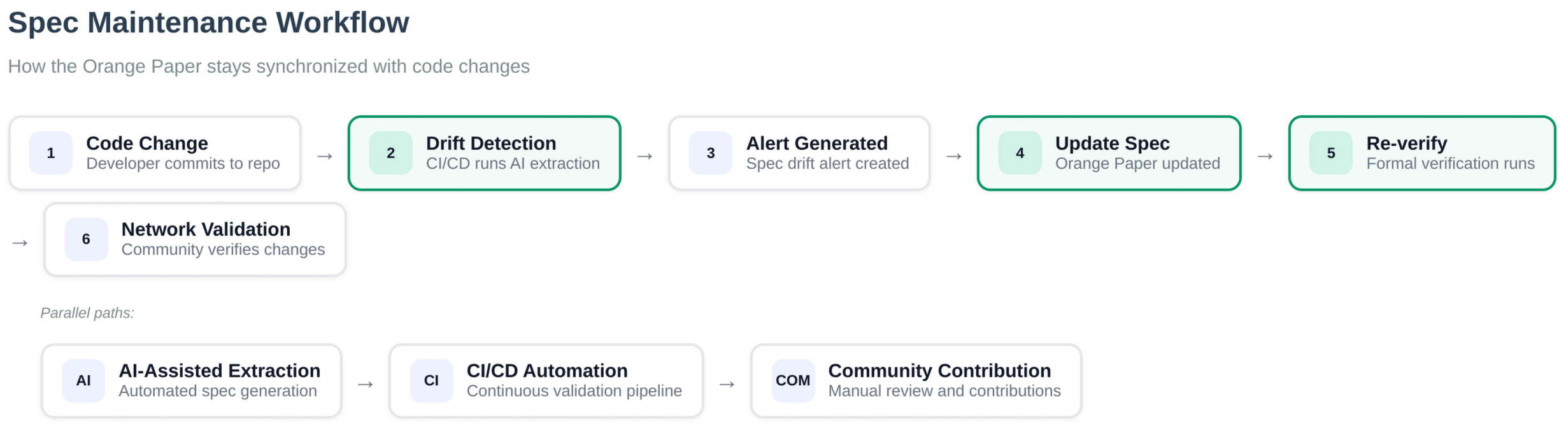
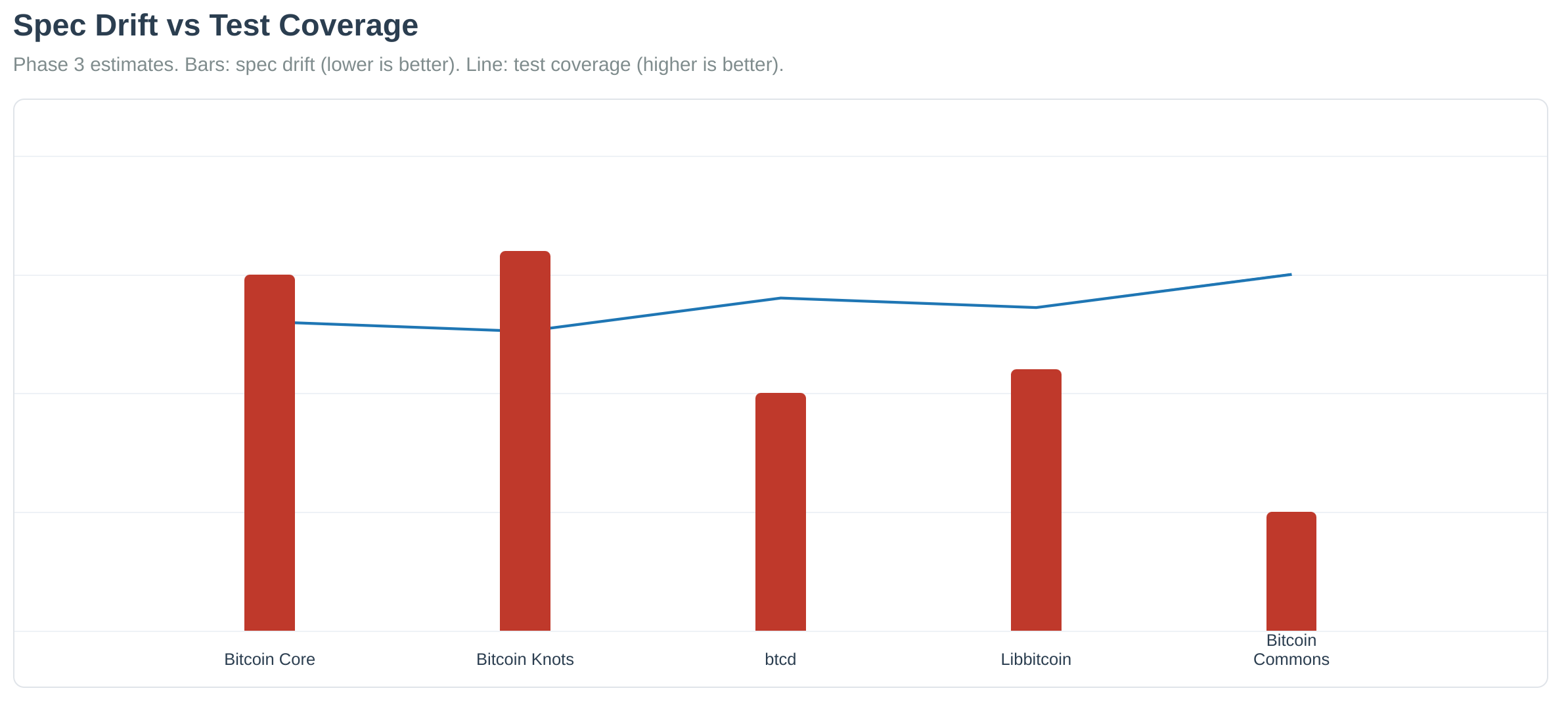
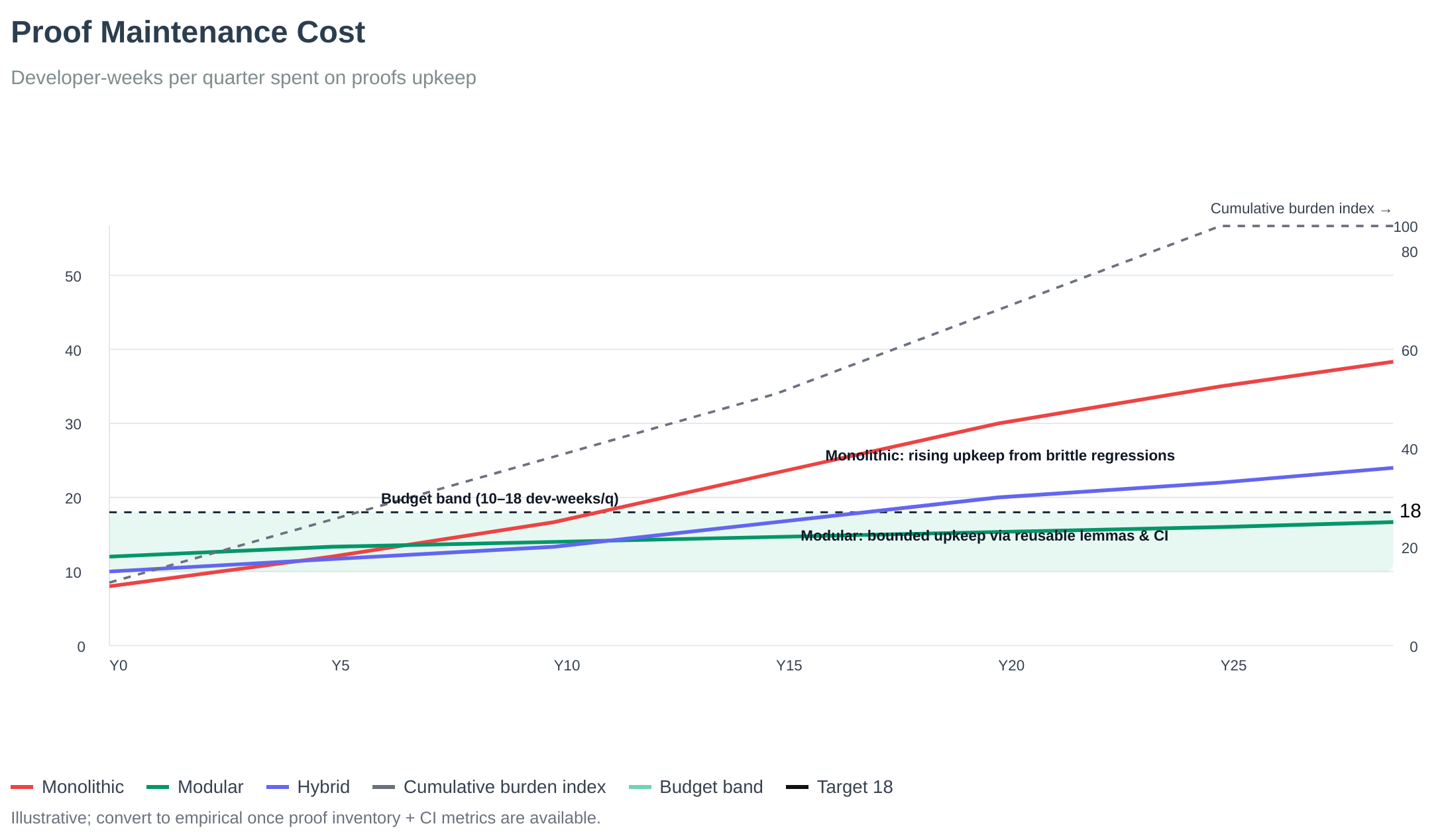
Status: Complete specification available at https://github.com/BTCDecoded/blvm-spec. The specification is actively maintained and verified against network behavior through automated testing.
4.4 BLVM Architecture
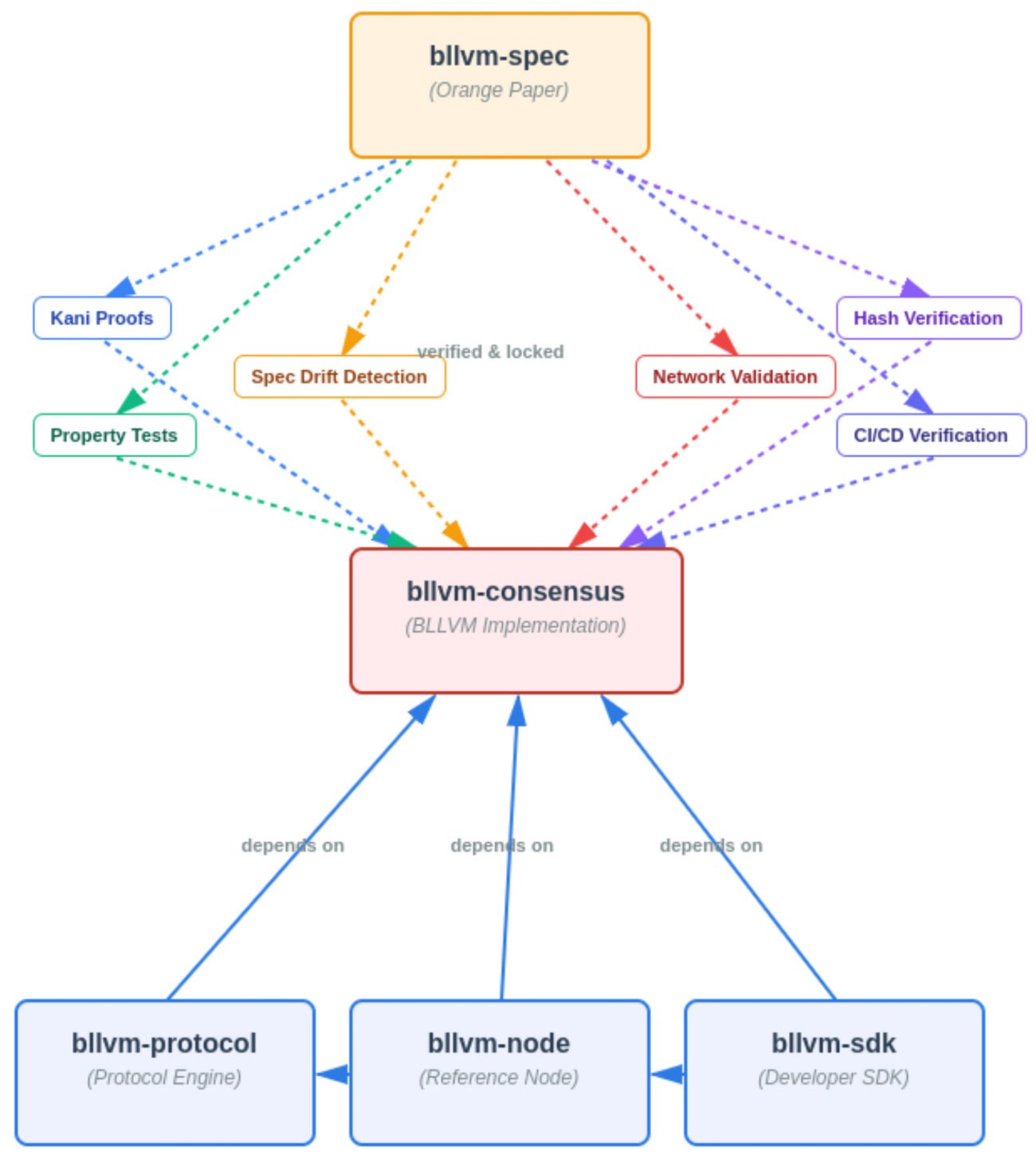
BLVM (Bitcoin LLVM) applies compiler-like infrastructure to Bitcoin implementations. The Orange Paper serves as an intermediate representation (IR), enabling reusable optimizations and multiple implementations.
Single Source of Truth. All consensus logic resides in blvm-consensus. Upper tiers (blvm-protocol, blvm-node) delegate validation calls with no duplicate implementations. Path dependencies ensure changes propagate immediately through Rust's type system.
Optimization Pipeline. Multiple passes apply. Formal verification (Kani model checking), property testing (proptest edge case discovery), LLVM compiler optimizations (opt-level 3, fat LTO, SIMD), and differential testing against network behavior. Scalable cloud infrastructure reduces proof execution time from hours to minutes at minimal cost.
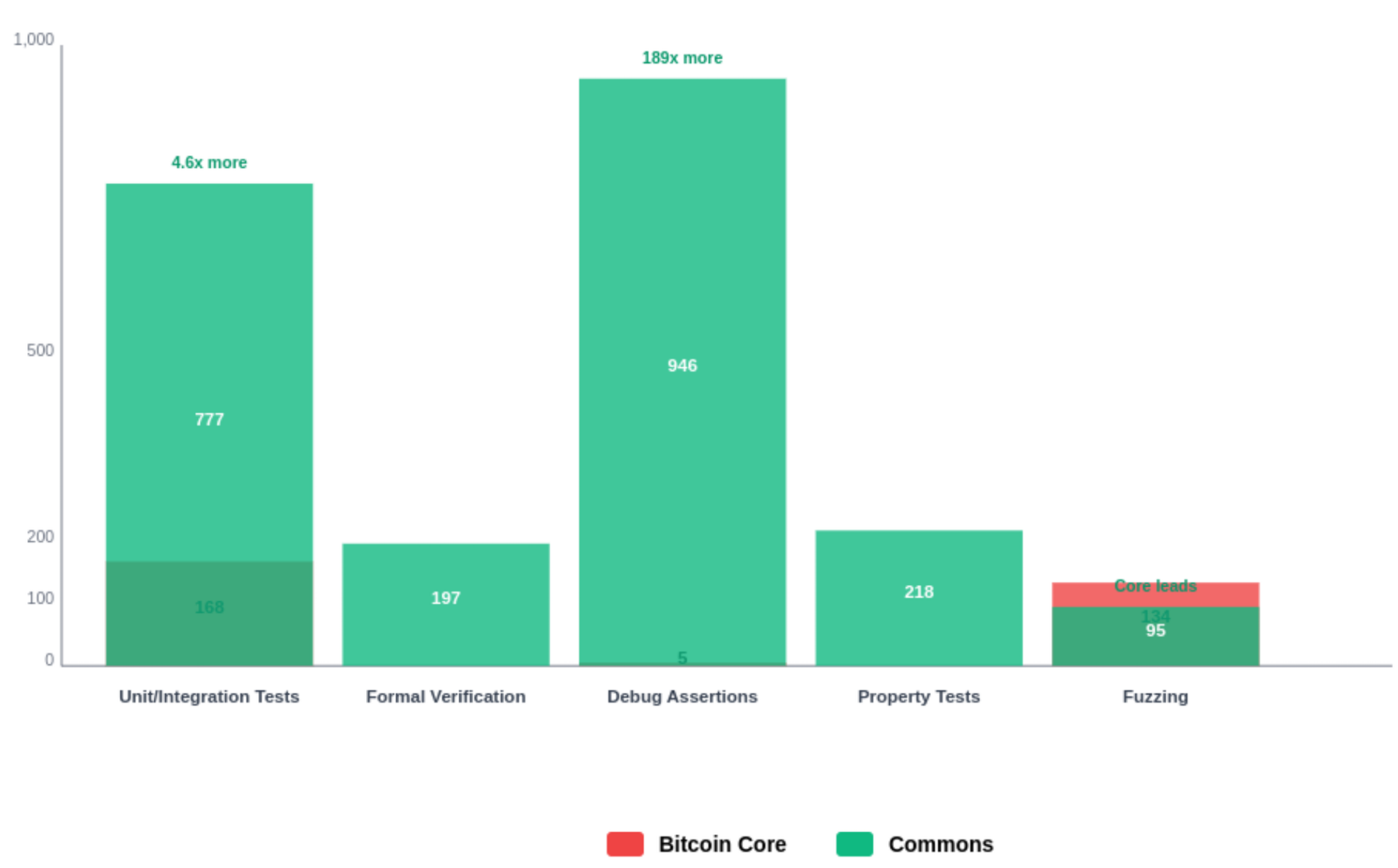
Formal verification in blvm-consensus applies to all tiers because all consensus decisions flow through verified functions. The dependency chain prevents bypassing verification.
5. Architectural Solution: Modular Governance
Two innovations work together: BLVM provides the mathematical foundation and compiler-like architecture (Orange Paper as IR, formal verification passes); Commons provides the governance framework (coordination without civil war). The modular architecture is where both innovations meet. BLVM ensures correctness through architectural enforcement; Commons ensures coordination through Cryptographic Polycentrism.
The governance architecture directly addresses power concentration problems identified in Bitcoin Core's development patterns (bitcoin-governance-research, 2026). Commons enforces distributed authority through cryptographic multisig requirements and mandatory review periods, preventing single points of control. This Cryptographic Polycentrism model creates multiple decision centers (repository layers, action tiers, emergency tiers) with mathematically enforced boundaries.
Two-Layer Architecture
The modular architecture consists of two layers that transform governance conflicts from political battles into architectural choices:
Layer 1: Mandatory Consensus (Base Node)
- Bitcoin's consensus rules, unchangeable without network agreement
- Cryptographically enforced, defines what "Bitcoin" means
- Examples: block validation, transaction validation, fork choice rules
Layer 2: Optional Modules (Extension System)
- User-controlled features that can be enabled or disabled
- Communities can fork/modify/compete, user choice determines winners
- Examples: Lightning Network, merge mining, Taproot Assets, privacy enhancements
Revenue Model
- Self-sustaining development through operational modules
- Marketplace module, governance announcement zaps, and optional merge mining module provide revenue streams
- Reduces reliance on grants, donations, or external funding
- Aligns incentives with usage and adoption, reducing capture risk
Module Isolation
Modules run in separate processes with strict boundaries:
Process Isolation Mechanisms:
- Each module runs in its own process space with isolated memory
- Modules communicate only through well-defined APIs
- Base node validates all blocks using Orange Paper specification regardless of enabled modules
- Module state completely separate from consensus state (UTXO set)
API Boundaries:
- Modules can only interact with base layer through documented interfaces
- No direct access to consensus functions or core data structures
- Module failures isolated and cannot propagate to base node
- Crash containment guaranteed by process boundaries
What modules CANNOT do: Modify consensus rules, alter block validation, cause network splits
What modules CAN do: Process their own state, crash without affecting base node
Containment Strategy
The modular architecture satisfies both camps simultaneously:
- "Don't Change Bitcoin" Camp: Gets pure Bitcoin base layer with no modifications
- "Make Bitcoin Useful" Camp: Gets optional features through modules
- Miners: Get additional revenue from merge mining
The Module System IS The Governance System: Instead of governing through committees deciding features, we govern through architecture enabling choice. The module system isn't just technical: it's the governance mechanism itself, implementing Ostrom's collective choice arrangements through user configuration, Hayek's competitive discovery through module competition, and Bitcoin's permissionless innovation through fork-ability.
Architecture Diagrams
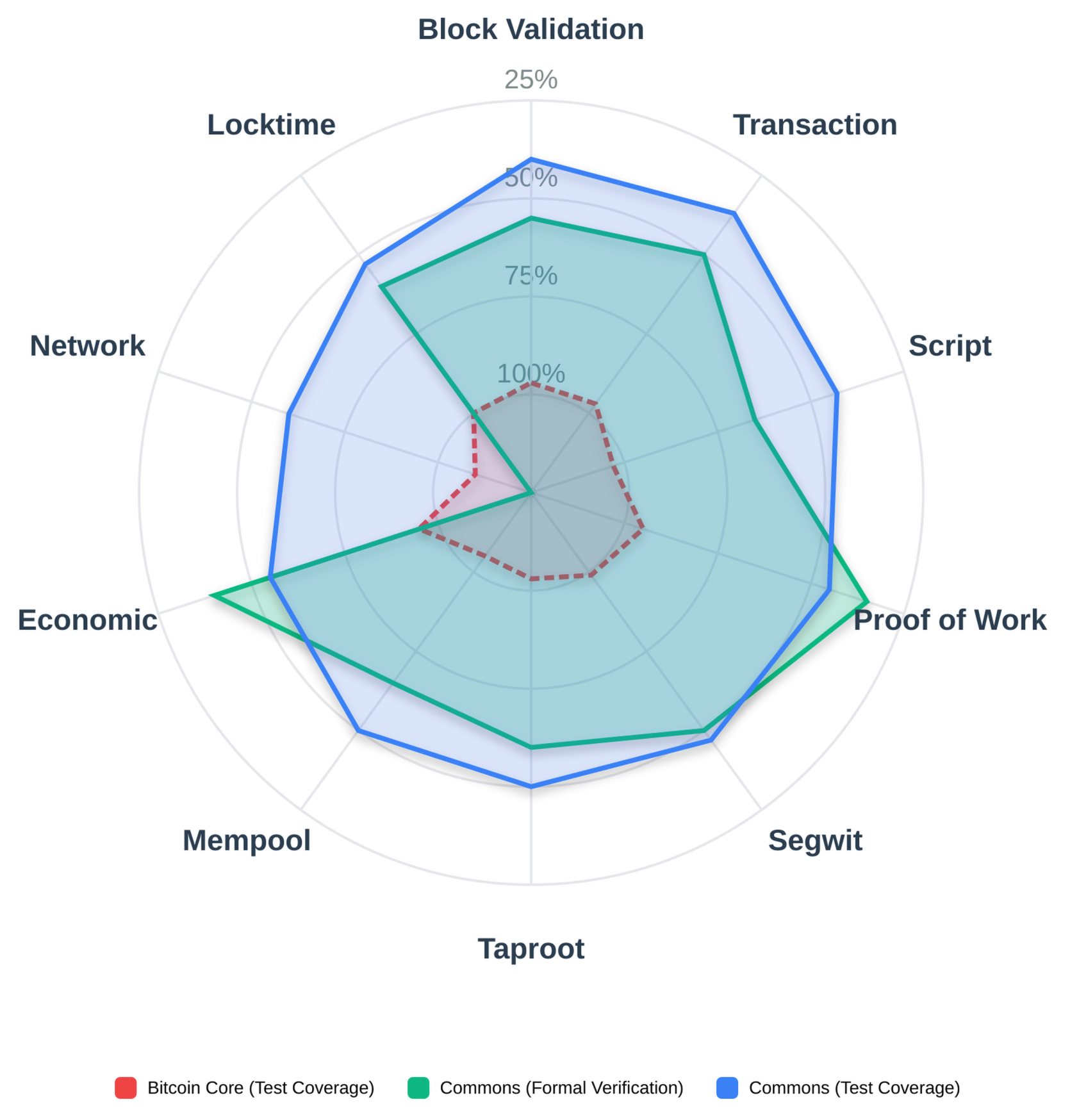
Fragmentation Analysis:
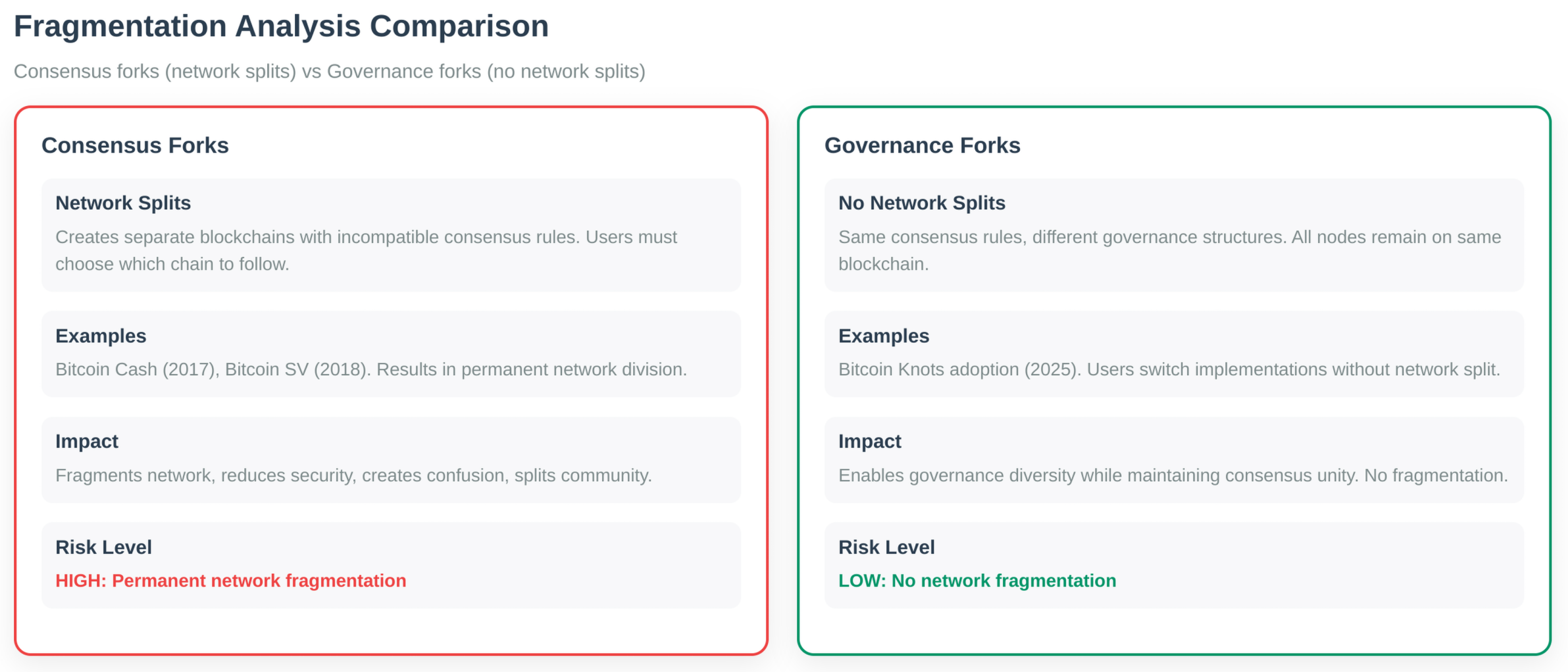
Governance forks preserve the consensus layer while allowing governance changes. Users can fork governance rules while keeping the same Bitcoin consensus. This is the ultimate accountability mechanism. Knots adoption (25% in five months) proved multiple implementations coexist without fragmentation.
Forking Process: Governance rulesets can be exported as versioned, signed packages containing action tiers, maintainers, cryptographic proofs, and semantic versioning. This enables users to fork governance while maintaining compatibility and verification.
Implementation Registry. A self-service registry provides permissionless listing of implementations via automated PR validation. If validation passes, merges occur automatically, demonstrating the framework's decentralized, cypherpunk-aligned nature.
6. Cryptographic Governance Enforcement
Commons implements Cryptographic Polycentrism through three complementary verification layers (distinct from repository layers) that ensure both real-time transparency and immutable historical proof. These verification layers create multiple independent centers of accountability, each enforcing governance boundaries through cryptographic proof:
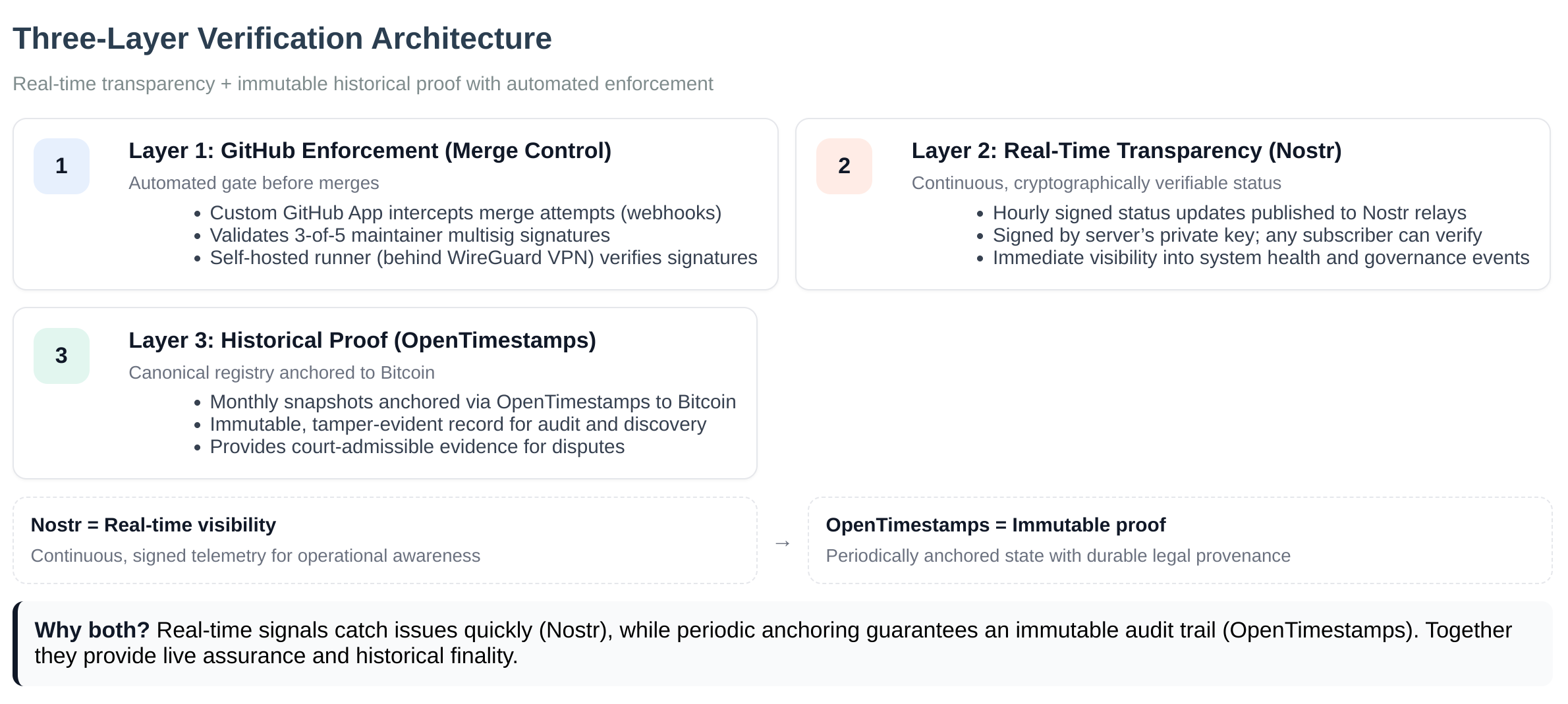
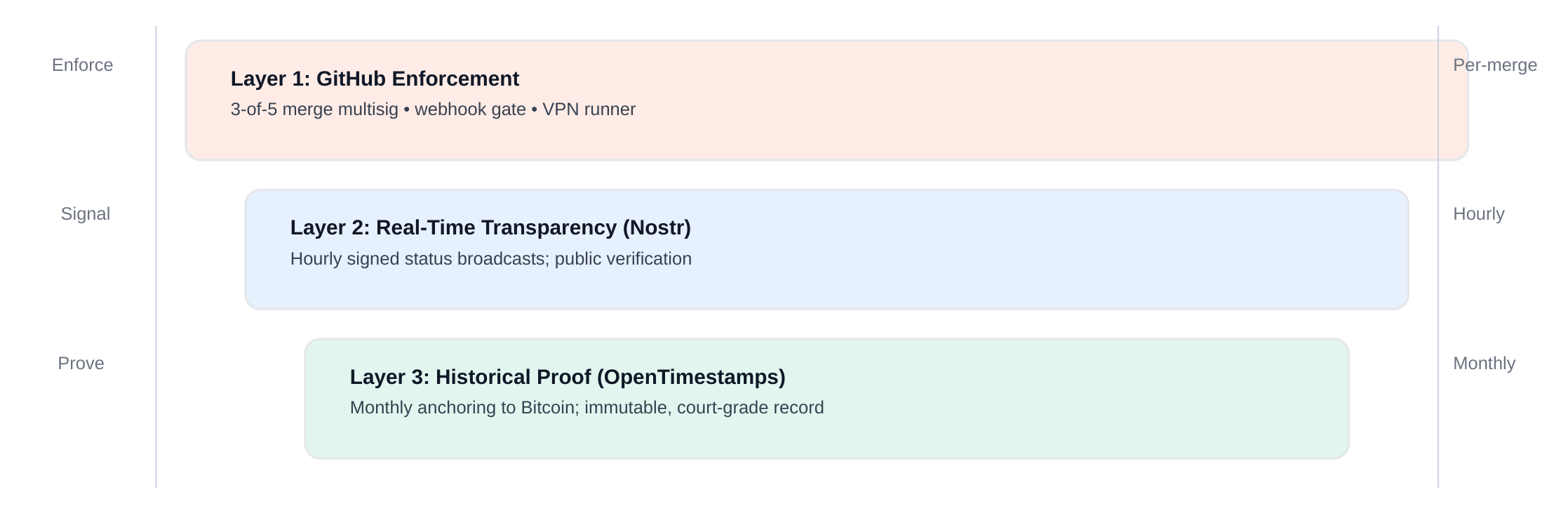
Layer 1: GitHub Enforcement (Merge Control)
- Custom GitHub App validates multisig requirements (varies by layer: 2-of-3 to 6-of-7)
- Self-hosted runner behind WireGuard VPN validates signatures using secp256k1
- Even repository admins cannot bypass cryptographic requirements
- Signature validation happens before merge approval
- Addresses Bitcoin Core's self-merge and zero-review patterns (bitcoin-governance-research, 2026) by requiring explicit cryptographic approval from multiple maintainers before any merge
Layer 2: Real-Time Transparency (Nostr)
- Hourly status updates published to Nostr relays
- Status includes: binary hash, config hash, recent merges, health metrics
- Cryptographically signed by server's unique NPUB (Nostr public key)
- Anyone can subscribe and verify server integrity in real-time
- Missing updates trigger community alerts within 2 hours
- Provides transparent monitoring that Bitcoin Core lacks, making governance patterns visible in real-time rather than requiring retrospective analysis (bitcoin-governance-research, 2026)
Layer 3: Immutable Proof (OpenTimestamps)
- Monthly canonical registry anchored to Bitcoin blockchain
- Critical events (key rotations, deployments) timestamped immediately
- Creates cryptographic proof of governance state at specific block height
- Provides court-admissible evidence for dispute resolution
- Works independently of any single server or relay
Cross-Layer Verification:
Three independent layers verify governance actions and each other. Risk at one layer does not compromise the others. This defense-in-depth approach ensures governance integrity even if one verification method is compromised.
Repository Hierarchy
Emergency Response
Commons implements a three-tier emergency system that activates when critical security issues require rapid response. Emergency tiers operate separately from action tiers and provide time-limited elevated authority with automatic expiration to prevent permanent emergency powers:
Critical Emergency (Network-threatening vulnerabilities):
- Activation: 5-of-7 signatures required
- Review period: 0 days (immediate response)
- Maximum duration: 7 days (no extensions)
- Examples: Inflation bugs, consensus fork risks, P2P network DoS vulnerabilities, remote code execution
Urgent Security Issue (Serious security issues):
- Activation: 5-of-7 signatures required
- Review period: 7 days
- Maximum duration: 30 days (1 extension allowed)
- Examples: Memory corruption vulnerabilities, privacy leaks, crash exploits, privilege escalation
Elevated Priority (Important but not critical):
- Activation: 5-of-7 signatures required
- Review period: 30 days
- Maximum duration: 90 days (2 extensions allowed)
- Examples: Competitive response needs, important bug fixes, performance degradation, ecosystem compatibility issues
The emergency system escalates requirements proportionally to severity while maintaining governance integrity through time limits and automatic expiration. All emergency actions require post-mortem documentation and are subject to review after expiration.
Security Architecture: Push-Only Design
Security Architecture Details:
- No HTTP Endpoints: Governance servers have no incoming HTTP endpoints (minimal exposure surface)
- VPN Isolation: Servers communicate outbound only through WireGuard VPN
- Self-Hosted Runner: GitHub runner behind WireGuard VPN for signature validation
- Data Flow: Server to GitHub (push) to Nostr (publish) to Bitcoin (anchor)
- Public Read Access: GitHub repo, Nostr relays, Bitcoin blockchain (read-only for public)
Attack Path Protection:
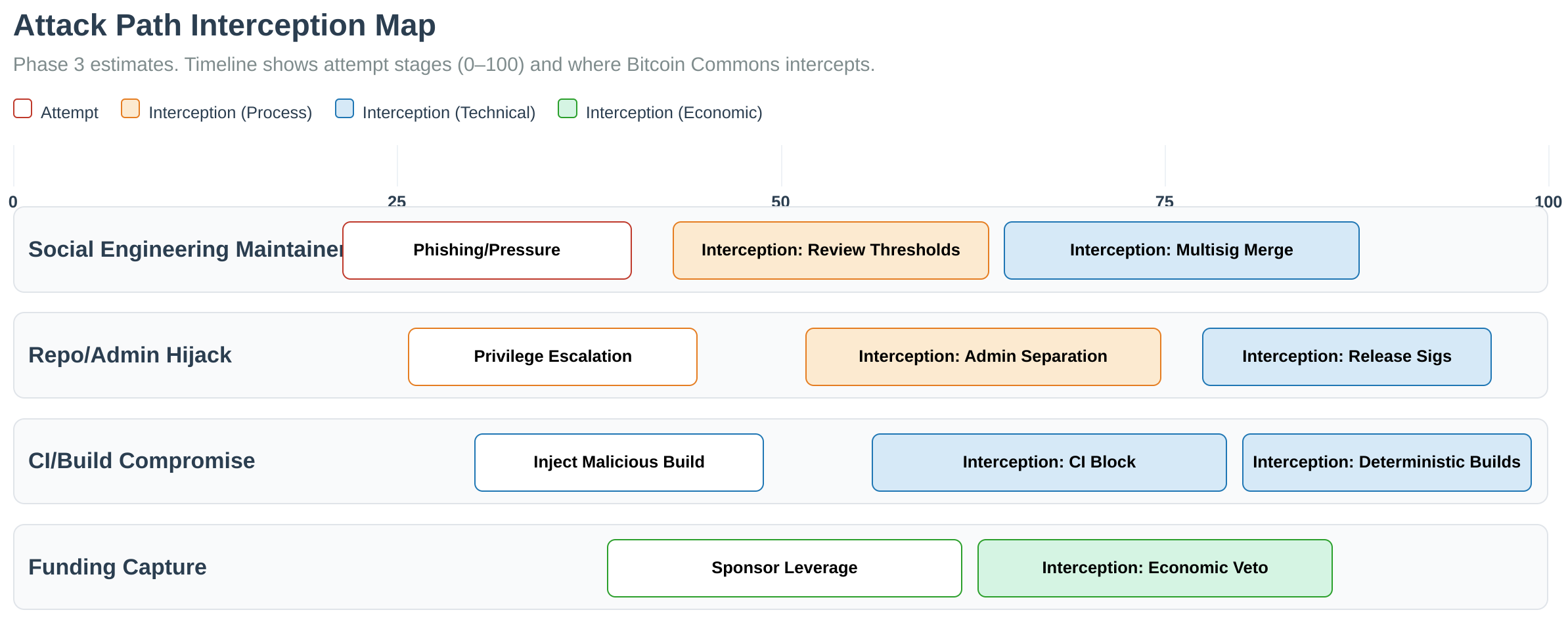
Multisig Threshold Details
Commons implements a 5-tier constitutional governance system that combines two dimensions: repository layers (where the change is made) and action tiers (what type of change is being made). When both apply, the most restrictive requirement wins (highest signature threshold and longest review period).
Repository Layers (Where):
- Layer 1-2 (Constitutional): Orange Paper and Consensus Proof - 6-of-7 signatures, 180-day review (365 days for consensus changes)
- Layer 3 (Implementation): Protocol Engine - 4-of-5 signatures, 90-day review
- Layer 4 (Application): BLVM Node - 3-of-5 signatures, 60-day review
- Layer 5 (Extension): SDK and modules - 2-of-3 signatures, 14-day review
Action Tiers (What):
- Tier 1 (Routine Maintenance): Bug fixes, documentation, optimizations - 3-of-5 signatures, 7-day review
- Tier 2 (Feature Changes): New RPC methods, P2P changes, wallet features - 4-of-5 signatures, 30-day review
- Tier 3 (Consensus-Adjacent): Changes affecting consensus validation code - 5-of-5 signatures, 90-day review
- Tier 4 (Emergency Actions): Critical security patches, network-threatening bugs - 4-of-5 signatures, 0-day review (with post-mortem required)
- Tier 5 (Governance Changes): Changes to governance rules themselves - 5-of-5 signatures, 180-day review
Most Restrictive Wins Rule:
When both layer and tier apply, the system takes the highest signature requirement and longest review period. For example:
- A routine bug fix (Tier 1) in the Protocol Engine (Layer 3) requires 4-of-5 signatures and 90-day review (Layer 3 wins)
- A new feature (Tier 2) in the SDK (Layer 5) requires 4-of-5 signatures and 30-day review (Tier 2 wins)
- A consensus change (Tier 3) in Orange Paper (Layer 1) requires 6-of-7 signatures and 180-day review (Layer 1 wins)
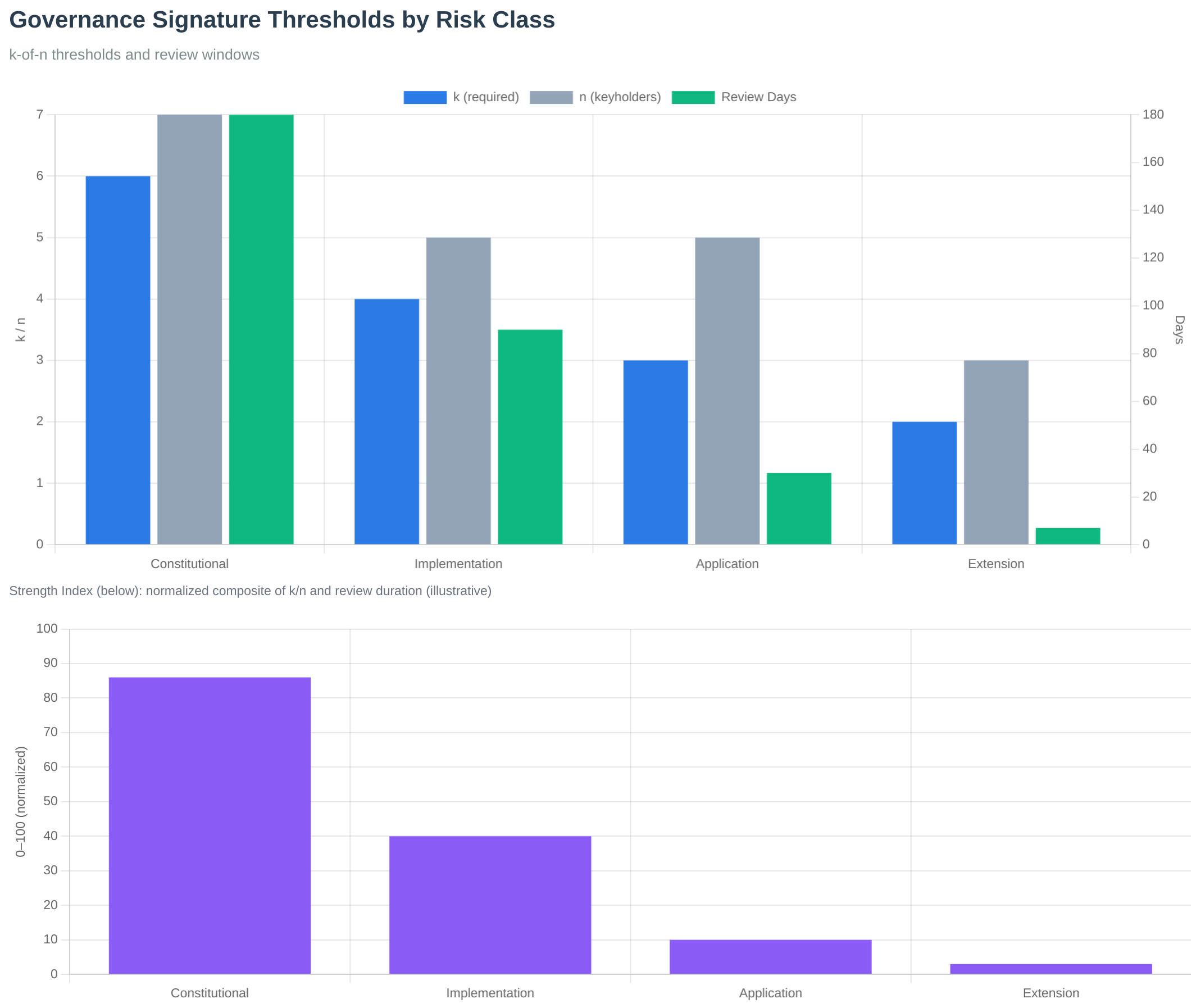
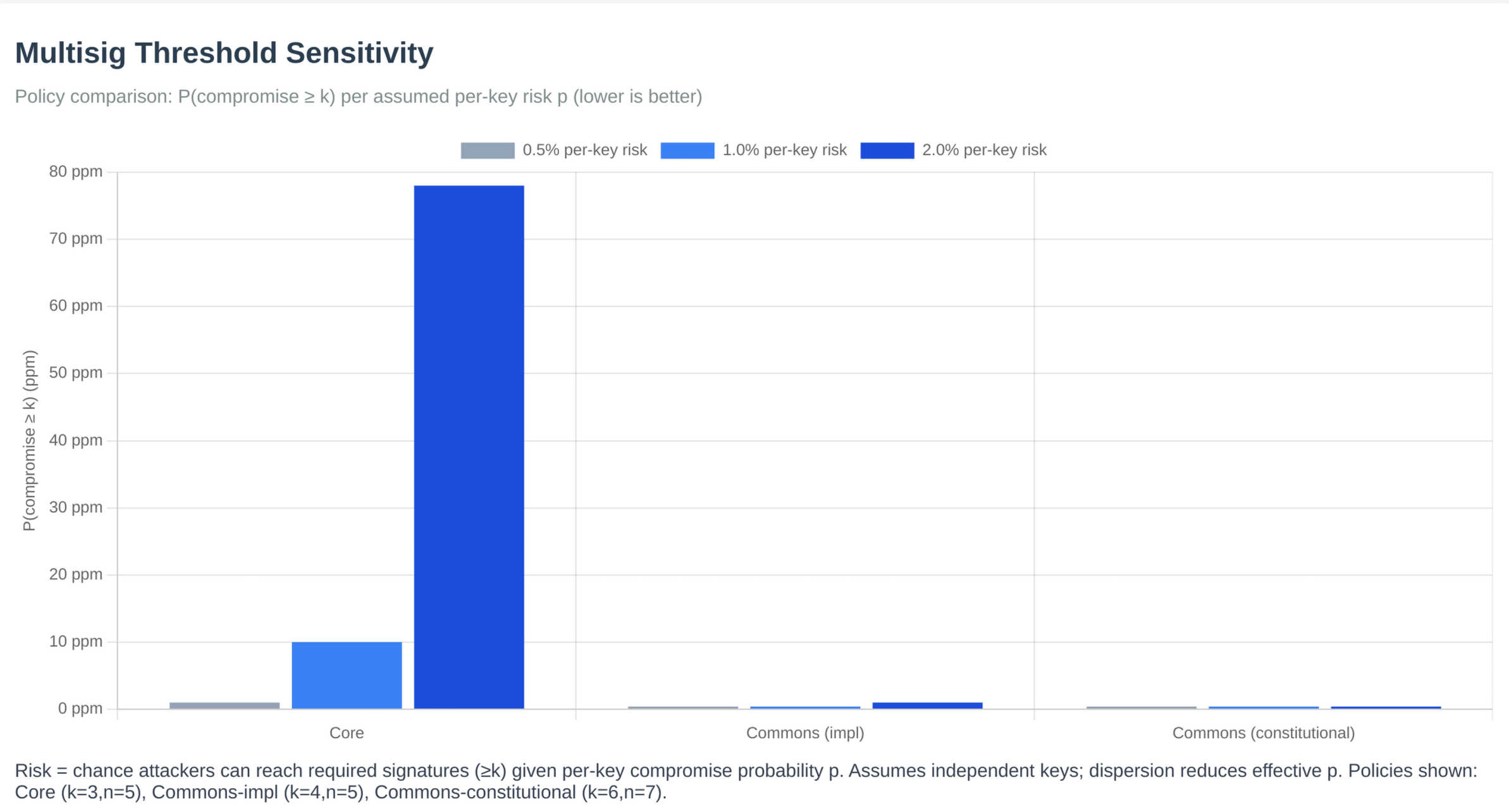
All signatures verified using secp256k1 (same curve as Bitcoin). GitHub App validates signatures before allowing merges. Even repository admins cannot bypass cryptographic requirements.
These thresholds directly address Bitcoin Core's power concentration problem (bitcoin-governance-research, 2026). Commons requires distributed approval: even the highest-risk changes (constitutional) require 6-of-7 signatures, ensuring no single maintainer or small group can control critical decisions. Mandatory review periods prevent rushed merges and ensure adequate community scrutiny, addressing the review quality issues identified in Bitcoin Core's development patterns. The dual-dimensional system (layers + tiers) provides additional safety: even routine changes in critical repositories require higher approval thresholds, preventing accidental or malicious changes to sensitive code.
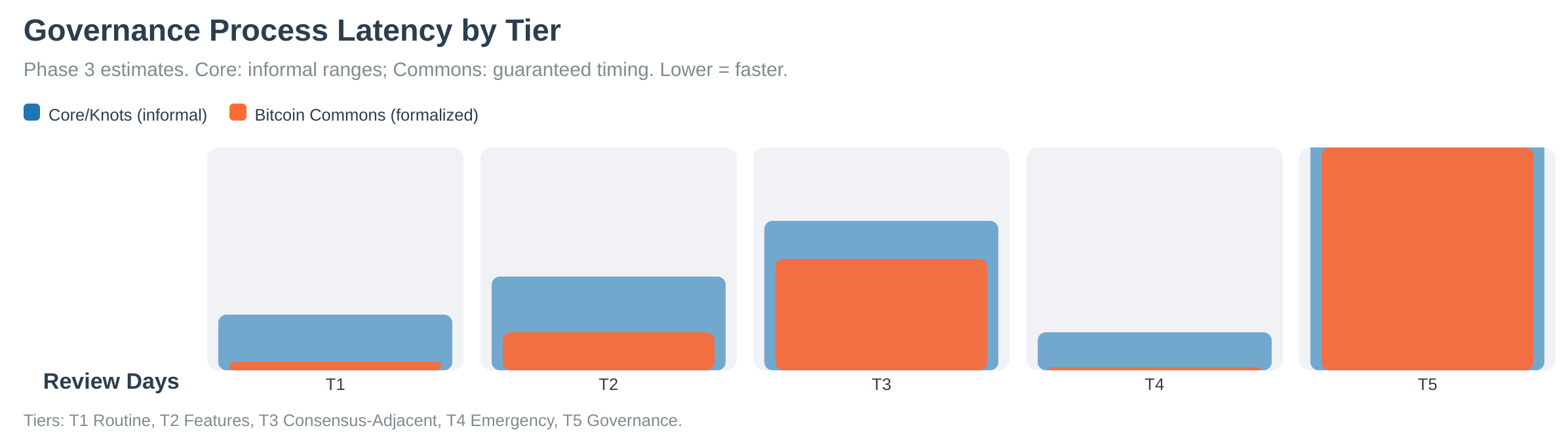
Governance Process and Latency
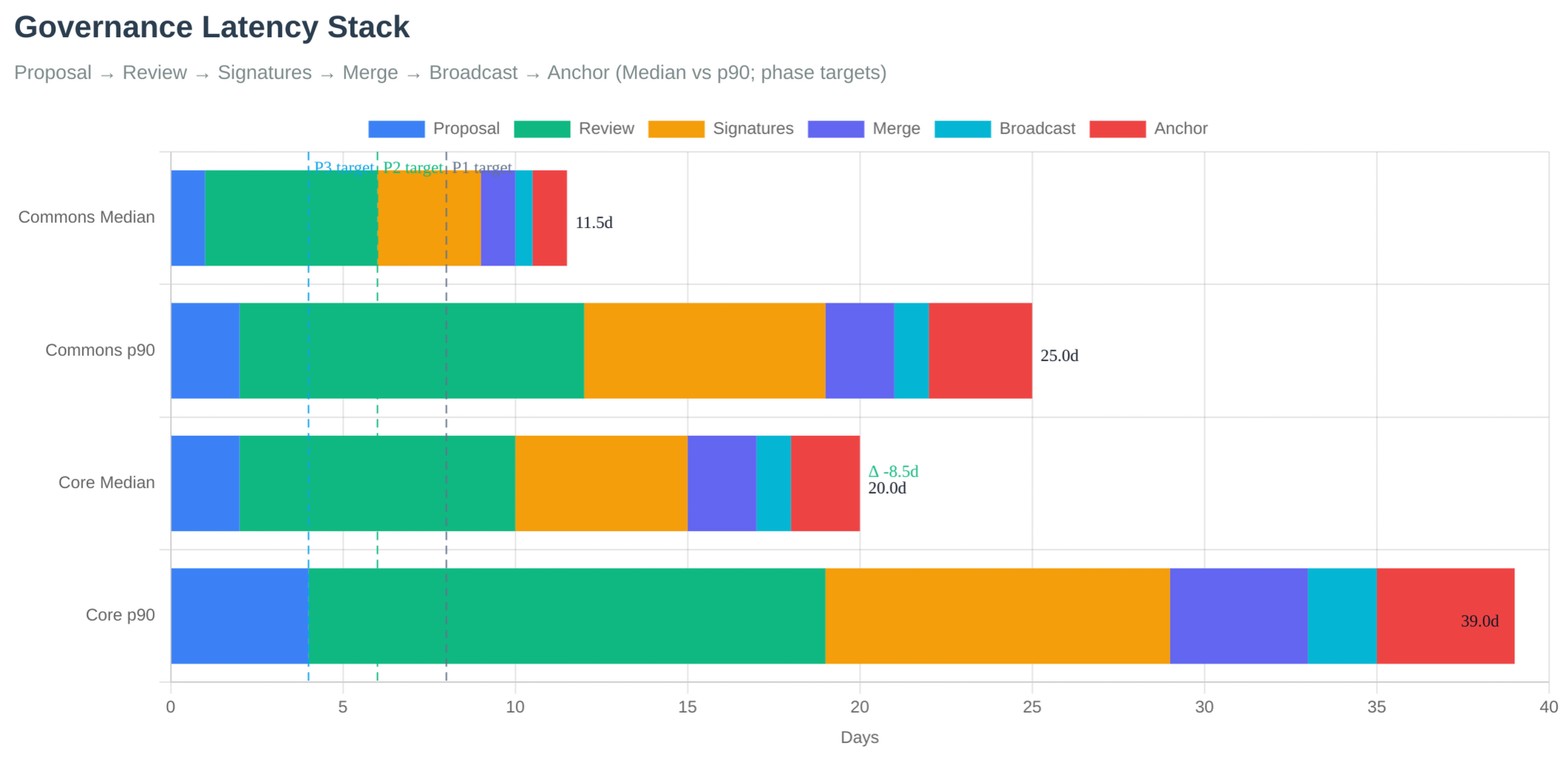
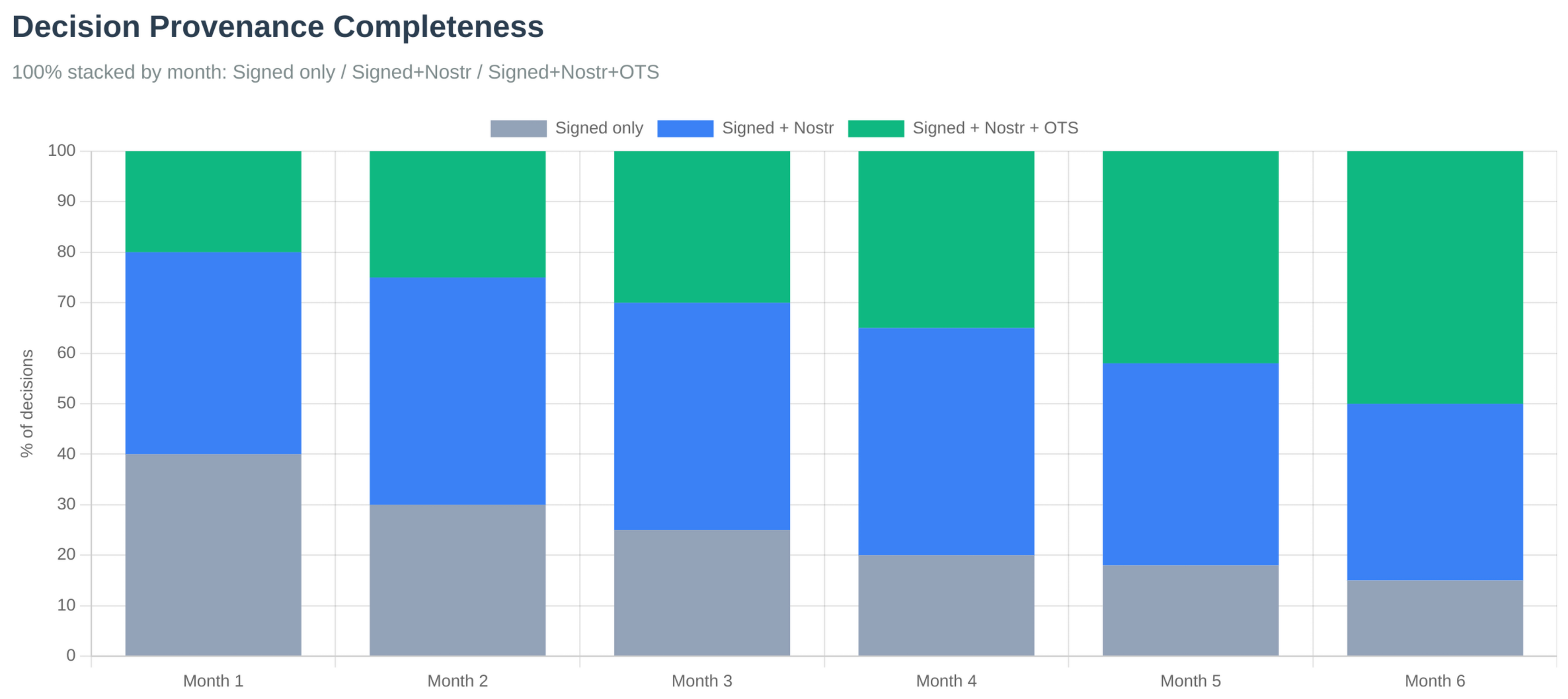
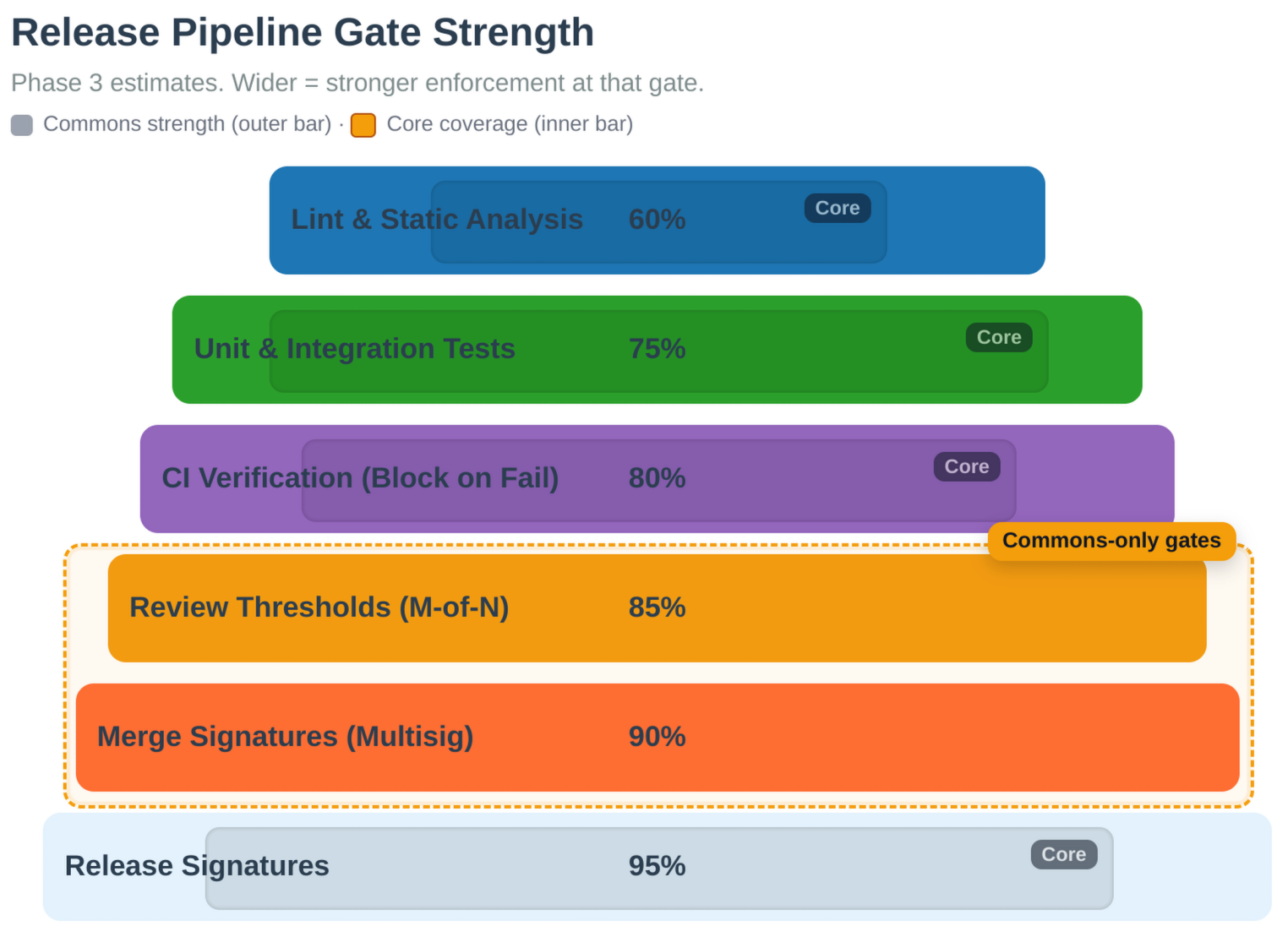
7. Economic Sustainability
The Funding Gap
Only $8.4 million from 13 organizations supported Bitcoin Core development in 2023, while the network reached a $2 trillion market cap (Hough, 2025). This 0.42% funding-to-market-cap ratio creates systemic vulnerabilities and limits Bitcoin's ability to scale safely.
Self-Sustaining Revenue Models
Bitcoin Commons operates modules to generate revenue for funding operations, reducing reliance on grants, donations, or external funding:
Marketplace Module: Enables distribution and monetization of modules.
Governance Announcement Zaps: Lightning Network zaps attached to governance announcements provide direct funding for governance operations.
Merge Mining Module: Coordinates merge mining for secondary chains, providing optional revenue when enabled.
These self-sustaining models align incentives with usage and adoption, making the system less vulnerable to capture than grant-dependent funding models.
Infrastructure Costs
- Server costs: $75-200/month for servers, VPN, and tooling
- Annual costs: under ~$30K including security audits
- Model aims to protect substantial Bitcoin value at low overhead
Success Metrics
- Level 1 (Sustainability): 1000+ nodes, revenue-positive operation
- Level 2 (Ecosystem Health): 3+ implementations with >15% combined node share
Success Level 1 proves sustainability. Success Level 2 proves the mission: implementation diversity becomes normal. We succeed when others copy the approach, not when we dominate the market.
8. Failure Modes & Mitigations
Governance Capture
Risk: Keyholder collusion or compromise
Mitigation: Multi-jurisdictional keyholders, transparent operation, fork-ready design. Current system easier to capture (target individuals privately, invisible control).
Regulatory Pressure
Risk: Authorities pressure keyholders to implement backdoors
Mitigation: Distributed keyholders across jurisdictions (no single jurisdiction can compel 3-of-5 threshold), visible capture attempts, modular containment
Technical Risks
Risk: Module consensus bugs, complexity explosion
Mitigation: Module isolation, formal verification, security audits
Social Risks
Risk: Community rejection, fork wars, reputation attacks
Mitigation: Focus on substance, build alternatives, let market decide; not asking permission, let code speak, coalition provides proof
Ultimate Protection
9. Implementation Status
Six Repositories
All repositories are public and active at https://github.com/BTCDecoded:
- Orange Paper (blvm-spec): Mathematical specification of Bitcoin consensus
- Consensus Proof (blvm-consensus): Formal verification of consensus rules
- Protocol Engine (blvm-protocol): Core protocol logic and state management
- BLVM Node (blvm-node): Complete Bitcoin implementation
- Developer SDK (blvm-sdk): Toolkit for building alternative Bitcoin implementations. Provides module composition framework for declaratively assembling custom Bitcoin nodes, plus governance cryptographic primitives.
- Governance (governance + blvm-commons): Configuration repository for governance rules and the GitHub App that enforces them
Current State
Phase 1 infrastructure provides substantial code implementing core capabilities. The system includes mathematical foundation and clean architecture. Governance infrastructure enables cryptographic enforcement.
Recent Technical Implementations
The BLVM Node implementation includes extensive Bitcoin protocol support:
BIP Implementations: Block filtering (BIP157/158), compact block relay (BIP152), hardware wallet support via PSBT (BIP174), Bech32m address encoding (BIP350/351), hierarchical deterministic wallets (BIP32/39/44), Bitcoin URI scheme with OS-level registration (BIP21), duplicate transaction prevention (BIP30), block version enforcement (BIP34), strict DER encoding (BIP66), NULLDUMMY checks (BIP147), and BIP90 validation.
Consistent Networking: Transport abstraction layer supporting both TCP and Iroh QUIC transports, with unified message routing across transport types. This enables nodes to choose transport based on network conditions while maintaining protocol compatibility.
Network Optimizations: Integrated coordination between compact blocks and block filtering for bandwidth efficiency. UTXO commitments support optional inclusion of block filters in responses. Transport-aware feature negotiation optimizes protocol usage based on available transports.
Advanced Networking: FIBRE (Fast Internet Bitcoin Relay Engine) implementation with Forward Error Correction (FEC) using Reed-Solomon encoding enables fast block propagation over UDP with resilience to packet loss. Package relay (BIP331) and privacy-preserving transaction relay options provide additional network efficiency and privacy capabilities.
Module System Architecture: Process-isolated module system with IPC communication, sandboxing, security validation, and module registry. Enables optional features (Lightning, merge mining, privacy enhancements) without affecting consensus or base node stability.
Stratum V2 + Merge Mining: Stratum V2 implementation with merge mining coordination for secondary chains (RSK, Namecoin, etc.). Multiplexed QUIC channels enable simultaneous mining of Bitcoin and secondary chains.
10. Development Roadmap

Phase 1 complete. Phase 2 activation requires meeting prerequisites below. Success metrics: Level 1 (sustainability) and Level 2 (ecosystem health through implementation diversity). Goal: create foundation for competing implementations, not replace Bitcoin Core.
Phase 1: Foundation
Phase 1 (Foundation) - Complete. Current capabilities and repositories are detailed in the implementation status section.
Phase 2: Governance Activation
Prerequisites (Must be met before activation):
- Comprehensive security audit by independent firm
- Public community validation period completed
- Production key management procedures operational
- Formal verification of critical consensus paths complete
- Legal review across multiple jurisdictions
- Miner commitment threshold reached (at least one major miner)
- No critical issues outstanding from Phase 1 review
Phase 2 Milestones:
Working Base Node: Complete BLVM Node implementation with full network compatibility (mainnet, testnet, regtest). Milestone: At least one major miner committed to merge mining model
Module System Architecture: Module API, loading system, and infrastructure. Milestone: Lightning module integration and module marketplace operational
Cryptographic Governance: Multisig infrastructure, distributed keyholder system, transparent processes, Governance App deployment. Milestone: Governance system is operational with full three-layer verification
Lightning Integration Module: Build Lightning Network module demonstrating architecture-based conflict resolution. Milestone: Lightning module is working and adopted
Merge Mining Support: Stratum V2 infrastructure and merge mining coordination. Milestone: Merge mining module operational (optional revenue source)
Module Marketplace: Build distribution infrastructure with quality control, security audits, and adoption metrics. Milestone: Module marketplace is operational
Revenue-Positive Operation: Achieve sustainable funding through operational modules, demonstrate economic model viability. Milestone: 1000+ node operators, revenue-positive operation (Level 1 success)
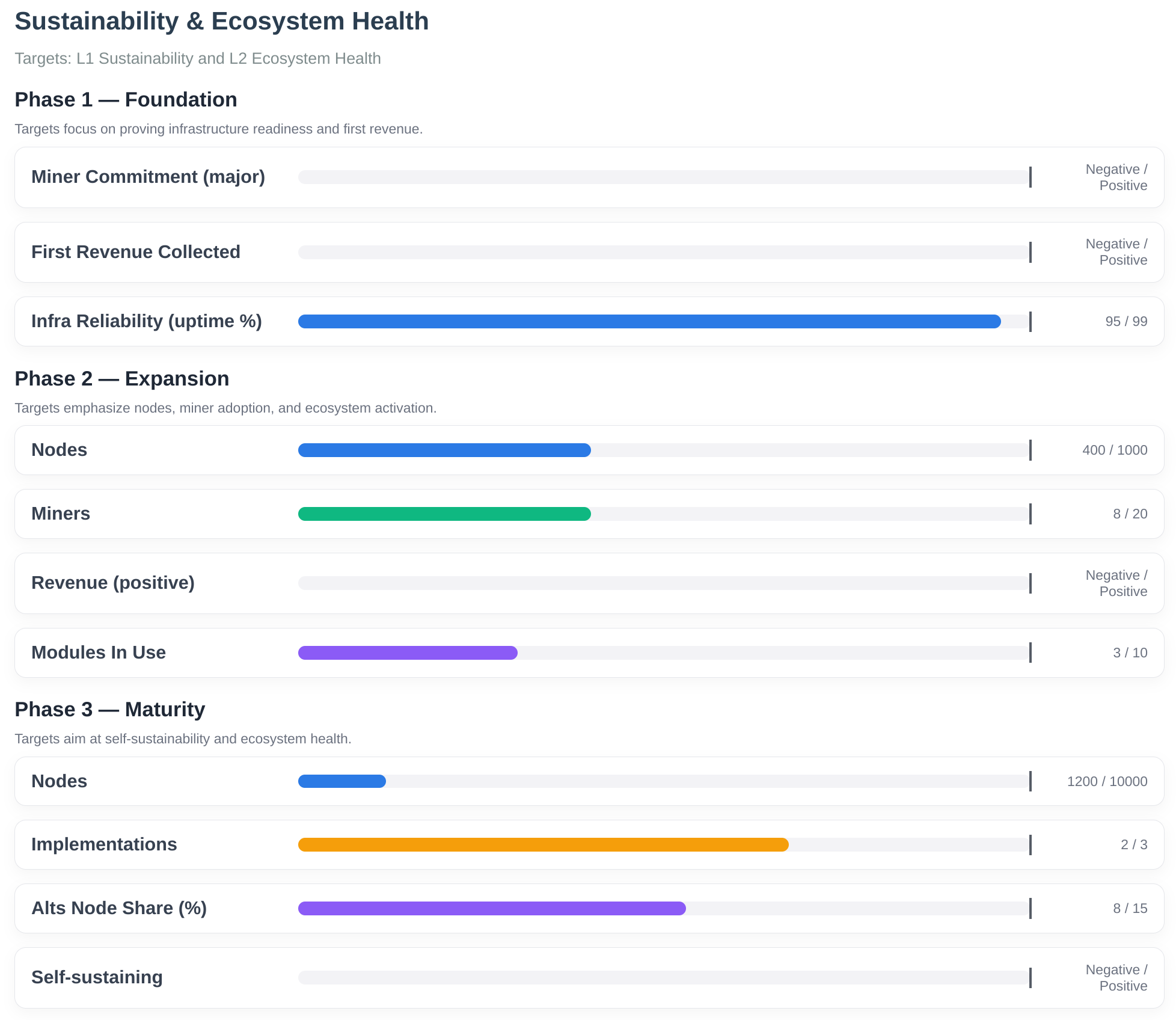
Phase 3: Maturity
Advanced Modules: Build privacy enhancement, alternative mempool policy, and smart contract integration modules. Milestone: 50+ available modules
Interoperability:
- Fedimint integration demonstrating infrastructure positioning
- Shared Iroh networking and LDK Lightning components enable natural interoperability
- Commons as infrastructure layer enabling other projects
Self-Sustaining Development: Achieve complete independence from external funding; demonstrate sustainable economic model; show governance system can operate without founder. Milestone: Self-sustaining without external funding
Operational Sustainability: Demonstrate sustainable operations through marketplace and governance modules; prove governance system effectiveness and economic viability
Production Deployment: Full mainnet governance infrastructure; first multisig merge, OpenTimestamps anchor, public monitoring operational; key rotation completed. Milestone: 10,000+ node operators, recognized as viable alternative
Recognition as Viable Alternative: Gain recognition from Bitcoin community; demonstrate technical superiority and governance advantages. Milestone: Accepted as legitimate Bitcoin implementation
Phase 4: Ecosystem Normalization
Reference Implementation: Become reference implementation for modular architecture; set standards and influence Bitcoin development ecosystem; enable multiple implementations using Commons SDK. Demonstrate governance system scalability.
Implementation Diversity Normalized: Make multiple implementations normal in Bitcoin; show Core is one option among many. Milestone: Implementation diversity normalized (Level 2 success)
Governance Model Adoption: Have governance model adopted by other projects; show governance principles are universal. Milestone: Governance model adopted by other projects
Strategic Positioning
Commons positions as infrastructure for multiple implementations, not a Core replacement. Success measured by ecosystem health and implementation diversity (Level 2 success), not market share. BitMEX validated Type 3 software forks; Commons adds specification, governance, and economics. Success when others build on the foundation, measured by ecosystem adoption.
Key Metrics
Key metrics align with Success Levels 1 and 2. Categories include:
Technical Metrics: Network compatibility, module adoption, revenue generation, user adoption
Governance Metrics: Decision transparency, economic alignment, anti-capture measures, sustainability
Ecosystem Metrics: Diverse implementations, module marketplace growth, developer adoption, community recognition
These metrics measure the health of the ecosystem, not just the success of Commons itself. For detailed risk analysis and mitigation strategies, see Section 8 (Failure Modes & Mitigations).
11. Conclusion
Bitcoin's governance vacuum represents its greatest vulnerability at multi-trillion dollar scale. The technical architecture is bulletproof, but the social architecture runs on gentleman's agreements. BLVM and Commons provide concrete, implementable solutions: BLVM ensures mathematical rigor; Commons applies Ostrom's principles, Hayek's competitive discovery, and Bitcoin's cryptographic enforcement to governance.
This isn't speculation. It's applying battle-tested principles from economics, social science, and cryptography to governance. Each framework addresses weaknesses in the others: cryptography makes Ostrom enforceable at scale, infrastructure enables Hayek's competition, and modularity plus fork-ability creates competitive discovery.
The foundation exists in public repositories, but implementation remains ongoing. The architecture is designed and the path is clear: the project's future depends on community participation.
The choice: decentralize the builders, or watch them become kings.
References
Academic Sources
- Ostrom, E. (1990). Governing the Commons: The Evolution of Institutions for Collective Action. Cambridge University Press.
- Hardin, G. (1968). The Tragedy of the Commons. Science, 162(3859), 1243-1248.
- Hayek, F. A. (1945). The Use of Knowledge in Society. American Economic Review, 35(4), 519-530.
- De Filippi, P., & Loveluck, B. (2016). The Invisible Politics of Bitcoin: Governance Crisis of a Decentralized Infrastructure. Internet Policy Review, 5(3).
- Walch, A. (2015). The Bitcoin Blockchain as Financial Market Infrastructure: A Consideration of Operational Risk. Fordham Law Review, 84(1), 1-58.
- Walch, A. (2017). The Path of the Blockchain Lexicon (and the Law). Vermont Law Review, 42(1), 1-30.
- Walch, A. (2019). Deconstructing 'Decentralization': Exploring the Core Claim of Crypto Systems. Cryptoassets: Legal, Regulatory, and Monetary Perspectives, 55-78.
- Hough, E. (2025). "Funding the Peer-to-Peer Ethos: A Network Analysis Proposal of Bitcoin's Technical & Social Collectives." Unpublished research proposal, INFO 4360: Communication Networks and Social Capital, Cornell University.
- Hough, E. (2022). "Evaluating The Diffusion & Adoption of Bitcoin: Through Network Effects, Public Sentiment & Self-Fulfilling Expectations Equilibrium." INFO 2040: Networks, Cornell University. Cornell Blogs - https://blogs.cornell.edu/info2040/2022/11/11/evaluating-the-diffusion-adoption-of-bitcoin-through-network-effects-public-sentiment-self-fulfilling-expectations-equil/
- Uzzi, B. (1997). Social Structure and Competition in Interfirm Networks: The Paradox of Embeddedness. Administrative Science Quarterly, 42(1), 35-67. https://doi.org/10.2307/2393808
- bitcoin-governance-research (2026). Comprehensive Quantitative Analysis of Bitcoin Core Development Governance. https://github.com/secsovereign/bitcoin-governance-research
Historical Sources
- Andresen, G. (2014). Bitcoin: The Future of Money? Princeton University, March 27, 2014.
- Hearn, M. (2016). The Resolution of the Bitcoin Experiment. Medium, January 15, 2016.
- BitMEX Research (2020). Bitcoin Core's Competition. BitMEX Research, January 2020.
Technical Sources
- CVE-2018-17144 (2018). Bitcoin Core Denial of Service Vulnerability. CVE Details. https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-17144
- Bitcoin Core Statistics. Public GitHub repository data.
- Bitcoin Optech Topics: High quality technical primers and references
- Merged mining: https://bitcoinops.org/en/topics/merged-mining/
- Stratum v2: https://bitcoinops.org/en/topics/stratum-v2/
- BOLT (Lightning) Specifications: https://github.com/lightning/bolts
Repository Links
- https://github.com/BTCDecoded/blvm-spec
- https://github.com/BTCDecoded/blvm-protocol
- https://github.com/BTCDecoded/blvm-consensus
- https://github.com/BTCDecoded/blvm-node
- https://github.com/BTCDecoded/blvm-sdk
- https://github.com/BTCDecoded/governance (governance configuration)
- https://github.com/BTCDecoded/blvm-commons (GitHub App that enforces governance)
System Status: For verified implementation status, see SYSTEM_STATUS.md in the BTCDecoded organization repository.
